Table of Contents
Office Macros and Security
Very often, cyber criminals try to exploit insecure settings or take advantage of risky use of macros in Microsoft Office products.
To protect yourself against harmful software, two factors have to be taken into account:
- Configure Microsoft Office so that macros will not be executed, at least not without checking them previously!
- Only allow a macro to be executed in an Office document if you know beyond any doubt the origin of the document and understand what the macro is needed for (e.g. a well-known document that has been in use for years in your working group and is located in its usual place where it has been residing for years)!
Deactivating Macros
To deactivate macros or to check your settings, please follow these steps:
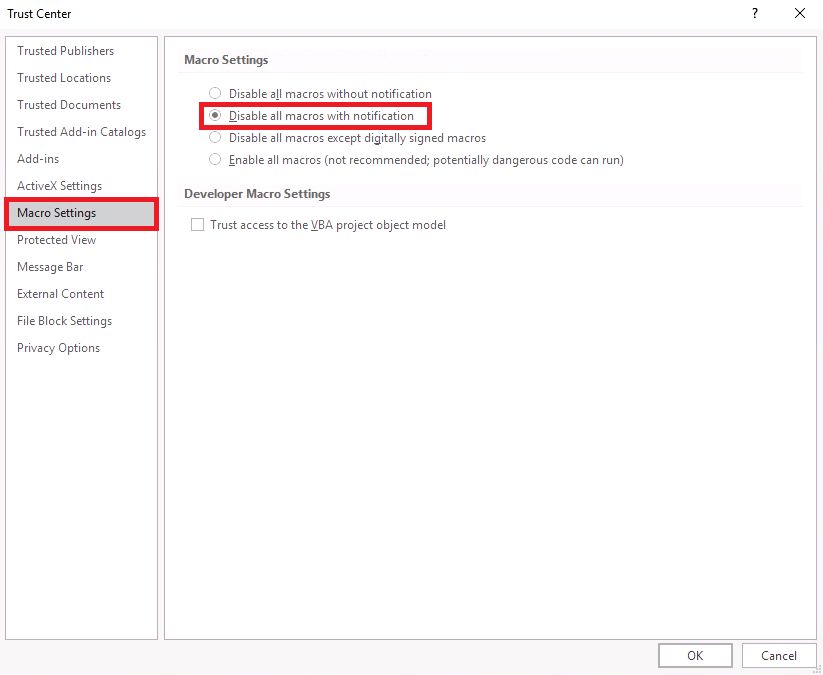
Available options are:
- Disable all macros without notification
- Disable all macros with notification
- Disable all macros except digitally signed macros
- Enable all macros (not recommended; potentially dangerous code can run)
The second option, marked red in image 5, is most recommendable. However, when opening a document with macros, you have to make a a qualified decision whether the macros in a document are hazardous or, on the contrary, can be executed without any risk. In case of even the slightest doubt, it is recommended to decide against execution of a macro (see also the example below).
The first option is the most secure, but it should only be chosen if you plan never to use documents with any macros. If the latter applies to you, then you should choose this option. Please be aware, though, that there won't even be an alert that a document contains macros, so in some cases, you may wonder why some document cannot be used.
The third option, which limits execution to digitally signed macros, is still relatively secure. Yet, in many cases unsigned macros are in use so that documents containing those will not function correctly. Furthermore, digitally signed macros may also occur in malware, so you'll have to find out and set up in the systems' configuration by whom macros may be signed and whose signature is trustworthy.
By no means, option 4, activating all macros, may be chosen. With this option, malware can be brought into action directly by opening a document is opened.
Questions about Activating Macros
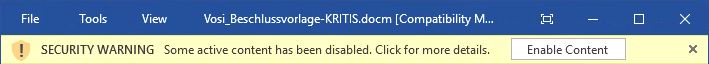
With the setting “Disable all macros with notification”, as described above, a security warning is shown when opening a document containing macros in an Office application (see image 6). The warning says: “SECURITY WARNING. Some active content has been disabled. Click for more details.”, and there is a button to “Enable Content”.
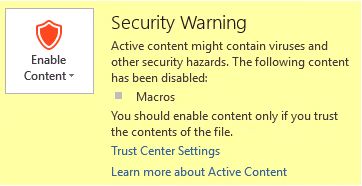
By clicking on the button, a window comes up which informs the user that there are macros in the document (see image 7) and, again, a button to “Enable Content”.
Content (i.e. the macros) should only be enabled if you are absolutely certain about the origin and the contents of the document in question, e.g. because the document has been in use for years and has always been stored in the same location or because you created it yourself). Do not enable content in documents received via e-mail unless you can exchange information on the document and the macros in it with the sender over a secure way of communication (e.g. telephone, personal meeting). An e-mail communication isn't sufficient in this case, as e-mails are all too often, and in hardly ever discernible ways, faked!